IDOR Hunting
ToxSec | A Guide to Insecure Direct Object Reference
Insecure Direct Object Reference (IDOR) remains a widespread vulnerability in web applications. While developers implement complex authentication systems and patch surface-level vulnerabilities, they frequently overlook the fundamental flaw of exposing direct references to internal objects.
At its core, IDOR exploits the failure to verify access controls when accessing resources through predictable references. The vulnerability is trivial to exploit yet consistently leads to data exposure and privilege escalation.
What is IDOR?
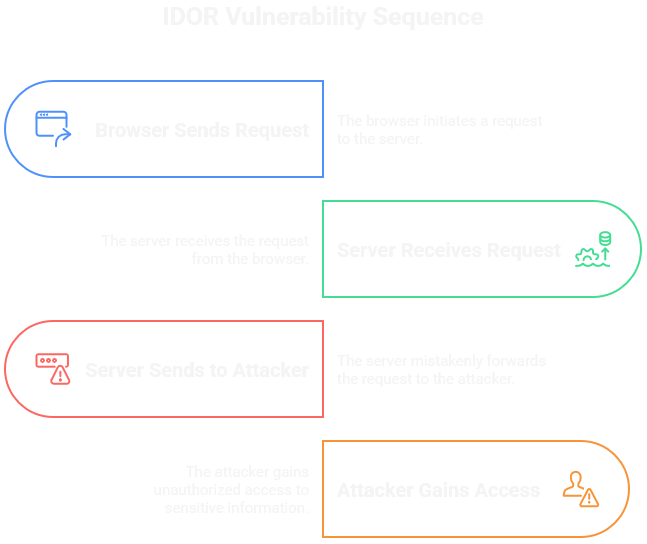
IDOR occurs when applications expose internal object references without validating access rights. A classic example: a user accesses their profile at:
https://example.com/account?id=123. The application retrieves data based on this ID parameter without verifying if the authenticated user should have access to that specific record. By simply modifying the ID parameter (id=124), an attacker can potentially access or modify other users data.
https://example.com/account?id=124.The vulnerability stems from a architectural flaw; trusting client-side parameters for direct object references. While applications may implement frontend restrictions and authentication checks, these controls become irrelevant when an attacker can directly manipulate backend references. This fundamental security oversight persists across web applications, APIs, and mobile backends, making IDOR a consistent source of critical security breaches.
0x01 Why is IDOR Important?
IDOR vulnerabilities persist as a security risk, consistently ranking in OWASP's Top 10 under Broken Access Control. Despite being well-documented and straightforward to prevent, IDOR continues to appear in production environments across all sectors, from startups to enterprise applications.
The attack surface is particularly attractive due to its low complexity and high impact ratio. Unlike other vulnerability classes that require complex exploitation chains or sophisticated bypass techniques, IDOR often presents immediate access to sensitive data or functionality through simple parameter manipulation. This combination of straightforward exploitation and severe impact makes IDOR a priority target for security researchers and malicious actors alike.
Two primary attack vectors dominate IDOR exploitation:
Direct Resource Access: Manipulation of identifiers to access unauthorized user data, financial records, or system files.
// User viewing their own profile picture
GET /api/users/avatar/1337
Authorization: Bearer eyJ0eXAiOiJKV1QiLC...
Response: 200 OK (image data)
// Viewing order details
GET /api/orders/12458
Authorization: Bearer eyJ0eXAiOiJKV1QiLC...
Response: {
"orderId": "12458",
"userId": "1337",
"items": [...],
"total": "149.99"
}
// Potential exploit
// Simply changing IDs to access other users' data
GET /api/users/avatar/1338
Authorization: Bearer eyJ0eXAiOiJKV1QiLC...
Response: 200 OK (different user's image)
GET /api/orders/12459
Authorization: Bearer eyJ0eXAiOiJKV1QiLC...
Response: {
"orderId": "12459",
"userId": "1338", // Another user's data
"items": [...],
"total": "249.99"
}Function-Level Bypass: Exploitation of administrative or privileged functions through direct reference manipulation.
// Admin deleting a user
DELETE /api/admin/users/1338
Authorization: Bearer eyJ0eXAiOiJKV1QiLC...
Role: admin
Response: 200 OK
// Admin viewing analytics
GET /api/admin/analytics/users
Authorization: Bearer eyJ0eXAiOiJKV1QiLC...
Role: admin
Response: {
"total_users": 1500,
"active_today": 300
}
// Potential exploit
// Regular user's token accessing admin endpoints
DELETE /api/admin/users/1338
Authorization: Bearer eyJ0eXAiOiJKV1QiLC... // Regular user token
Response: 200 OK // Successfully deleted user despite not being admin
Modern development practices often exacerbate IDOR risks. The rapid adoption of API-first architectures and microservices has expanded the attack surface. Each endpoint becomes a potential IDOR vector, especially in systems where frontend and backend services are decoupled. Security researchers regularly uncover critical IDOR vulnerabilities in production APIs that expose user databases or allow unauthorized administrative actions.
The tech debt associated with IDOR vulnerabilities typically requires architectural changes to resolve. Simply adding access control checks to individual endpoints often results in inconsistent implementation and bypass opportunities.
0x02 IDOR Explained
IDOR vulnerabilities manifest when applications fail to implement proper access control mechanisms at the resource level. While most developers understand the importance of authentication, they often overlook the critical distinction between authentication and authorization - leading to exploitable IDOR conditions.
Consider a typical web application architecture. When a user requests a resource, the application typically follows this flow:
Authentication check confirms the user's identity
Application retrieves the requested resource using a direct reference
Resource is returned to the user
The vulnerability occurs in step 2, where the application fails to verify if the authenticated user should have access to the requested resource. This oversight creates a direct path to unauthorized access.
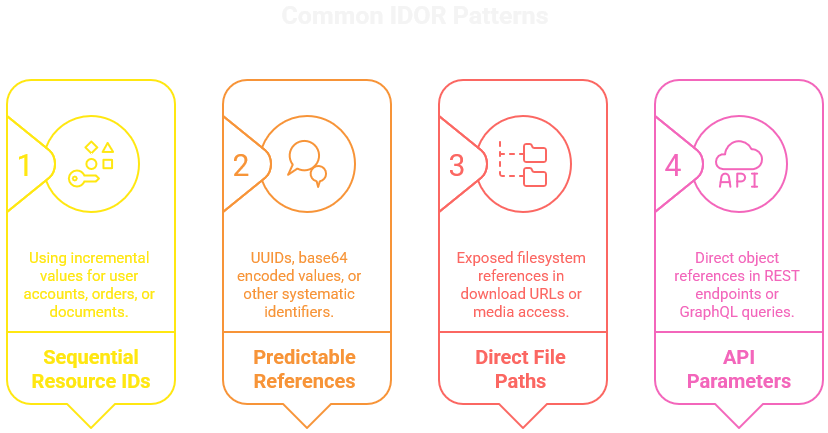
IDOR patterns include:
// Sequential IDs
/api/documents/1
/api/documents/2
/api/documents/3
// UUID patterns
/api/files/b4f23c-a618-4744-9127-5c96ef39b741
// Base64 encoded IDs
/api/users/MTIzNDU2Nzg5
// Nested resources
/api/organizations/1/users/2/documents/3
// Alternative API versions
/api/v1/users/1337 // Might have different access controls than
/api/v2/users/1337Modern applications often expose these references across multiple layers. A single user action might trigger calls to several microservices, each potentially vulnerable to IDOR. This complexity makes comprehensive access control increasingly challenging to implement and verify.
The exploitation process typically involves:
Identifying direct object references in application requests
Understanding the reference structure and patterns
Manipulating references to access unauthorized resources
Automating the process to enumerate accessible objects
IDOR vulnerabilities frequently chain with other security issues. For example, an IDOR might expose user IDs that can be used in subsequent attacks, or provide access to files that contain sensitive configuration data. These chained attacks can escalate a simple IDOR into a complete system compromise.
Real-world IDOR vulnerabilities often appear in seemingly benign functionality. Profile picture uploads might expose a direct file reference. Order history APIs might accept user IDs without verification. Document management systems might use predictable URLs for file access. Each of these scenarios presents an opportunity for unauthorized access through reference manipulation.
0x03 Where to Look for IDOR
IDOR vulnerabilities surface across multiple application layers, but certain patterns and locations consistently yield results. Understanding these common vectors streamlines the identification process and improves detection rates.
URL Parameters and Query Strings The most obvious IDOR vectors appear in URLs. Look for endpoints handling user data, especially those containing numeric IDs, UUIDs, or encoded strings. Pay particular attention to features that access user-specific information like profiles, documents, or account settings. These endpoints often implement authentication but neglect proper authorization checks. For example:
@app.route('/api/user/profile/<user_id>', methods=['GET'])
def get_user_profile(user_id):
# No authorization check, only authentication
if not is_authenticated():
return jsonify({'error': 'Authentication required'}), 401
# Directly uses user supplied ID - VULNERABLE
user_data = db.query(f"SELECT * FROM users WHERE id = {user_id}")
return jsonify(user_data)
Applications heavily rely on API calls, creating extensive IDOR attack surfaces. Focus on:
REST endpoints handling CRUD operations
GraphQL queries exposing direct object references
Mobile app APIs, which often implement weaker server-side controls
Internal APIs exposed through proxy endpoints
Example:
// Vulnerable API endpoint accepting all parameters
app.put('/api/users/:id', (req, res) => {
// Directly using request body - VULNERABLE
User.update(req.params.id, req.body);
});
Request Bodies and Hidden Fields While less obvious than URL parameters, POST request bodies frequently contain direct object references. Examine:
Form submissions handling user data
AJAX requests managing resource access
File upload/download functionality
Batch operation endpoints
State Management Applications often expose object references through state management mechanisms:
JWT tokens containing user IDs or resource references
Session variables storing access parameters
Local storage containing cached object references
Pay special attention to endpoints handling sensitive operations or data access. While these often implement stricter authentication controls, monitoring normal application traffic reveals how resources are referenced and accessed - providing crucial patterns for identifying potential IDOR conditions.
0x04 How to Test for IDOR
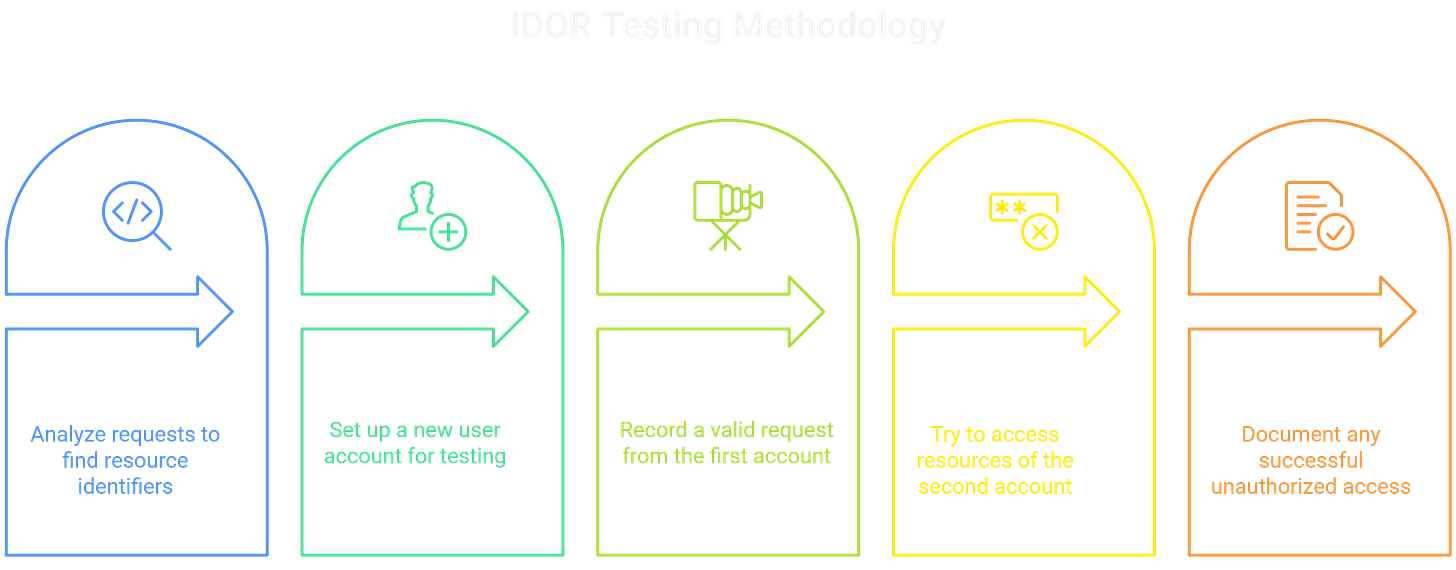
Testing for IDOR requires a methodical approach combining manual analysis and automated testing. The key is understanding how the application handles object references and systematically probing these handling mechanisms for authorization failures.
Start by mapping the application's functionality while intercepting all requests. Pay attention to how the application references resources across different features. Establish patterns in ID formats, URL structures, and API endpoints. This baseline helps identify potential IDOR vectors and informs testing strategies.
Manual Testing Methodology Begin with a legitimate user account and document all actions that access or modify resources.
Parameter Analysis Resource references appear in multiple formats. Test for IDOR when encountering:
Sequential IDs (increment/decrement values)
Base64 encoded strings (decode and modify)
UUIDs (collect and reuse across requests)
Hashed values (analyze pattern and predictability)
HTTP Method Manipulation Don't limit testing to the original HTTP method. An endpoint might verify authorization on GET requests but fail to implement checks on PUT or POST methods. Test all HTTP methods against identified endpoints, particularly for API calls.
Common Bypass Techniques When initial tests fail, try these bypass methods:
Modify the request content-type
Use different API versions
Change parameter encoding
Submit nested objects
Manipulate array inputs
Response Analysis Don't just focus on successful access. Analyze application responses for:
Error messages revealing resource existence
Different response times indicating valid resources
Subtle changes in response formats
Leaked information in error states
The most critical IDOR vulnerabilities often appear in unexpected places or through subtle variations in request handling. Maintain detailed testing notes and systematically work through all application functionality. A methodical approach yields better results than random testing.
0x05 Common IDOR Variants
Blind IDOR represents a subtle class of vulnerability where successful access isn't immediately apparent. Instead, the application leaks access information through timing differences, error messages, response codes, or content length variations. Consider this endpoint:
@app.route('/api/document/<doc_id>')
def get_document(doc_id):
try:
doc = Document.get(doc_id)
if not user_has_access(doc):
time.sleep(1) # Artificial delay
return {'error': 'Not found'}, 404
return doc.content
except DocumentNotFound:
return {'error': 'Not found'}, 404Here, timing analysis reveals valid documents through delayed responses, even when access is denied.
Chained IDOR exploits multiple vulnerabilities in sequence. An initial IDOR might expose internal references, enabling access to additional endpoints and escalating impact. Parameter pollution extends this by exploiting how applications handle multiple input sources - combining URL parameters with POST data, or leveraging nested JSON structures to bypass access controls.
Race condition IDORs emerge during state transitions like resource creation or ownership transfers. These time-sensitive vulnerabilities exploit gaps in access control during multi-step operations:
@app.route('/api/transfer/document', methods=['POST'])
def transfer_document():
doc = Document.get(request.json['doc_id'])
new_owner = User.get(request.json['new_owner'])
if doc.owner_id != current_user.id:
return {'error': 'Unauthorized'}, 403
# Race condition window between check and transfer
doc.owner_id = new_owner.id
db.commit()Format manipulation attacks target how applications handle different reference formats. Converting between numeric and string representations, modifying encoding schemes, or altering parameter structures can reveal IDOR vulnerabilities that standard testing might miss.
Each variant requires specific testing approaches, but understanding these patterns helps develop comprehensive detection strategies and more effective security controls.
0x06 Debrief - IDOR Vulnerabilities
IDOR vulnerabilities persist because they exploit a fundamental gap between authentication and authorization. While authentication systems continue to evolve and improve, authorization remains a complex challenge that many applications fail to properly address.
The impact of IDOR vulnerabilities continues to grow as applications handle increasingly sensitive data and critical functionality. IDOR is often found when testing APIs.
If you want to continue reading about web security, take a look at the API testing article here.